ADVERSARY INTELLIGENCE ENGINE
Weaponizing Threat Intelligence
From raw threat reporting to an evidence-backed adversary intelligence catalog
Sign Up
A Unified View of Adversary Behavior
Browse normalized threat actions, actor profiles, and attack paths across IT and OT systems. Each view is schema-driven and built for reuse in detection and response workflows.
Source Intake
Threat reports, advisories, knowledge bases, and curated collections
Extract & Version
Text extraction (incl. PDFs) plus change detection and provenance
Reference Expansion
Firecrawl-powered link capture to enrich documents with cited context
Normalize
Strict schemas and consistent IDs across documents, actors, and techniques
SAIRA Max
Classify documents, analyze actors/techniques, and generate structured actions
Review & Enhance
Dedup + quality review, then SAIRA Research agent improvements
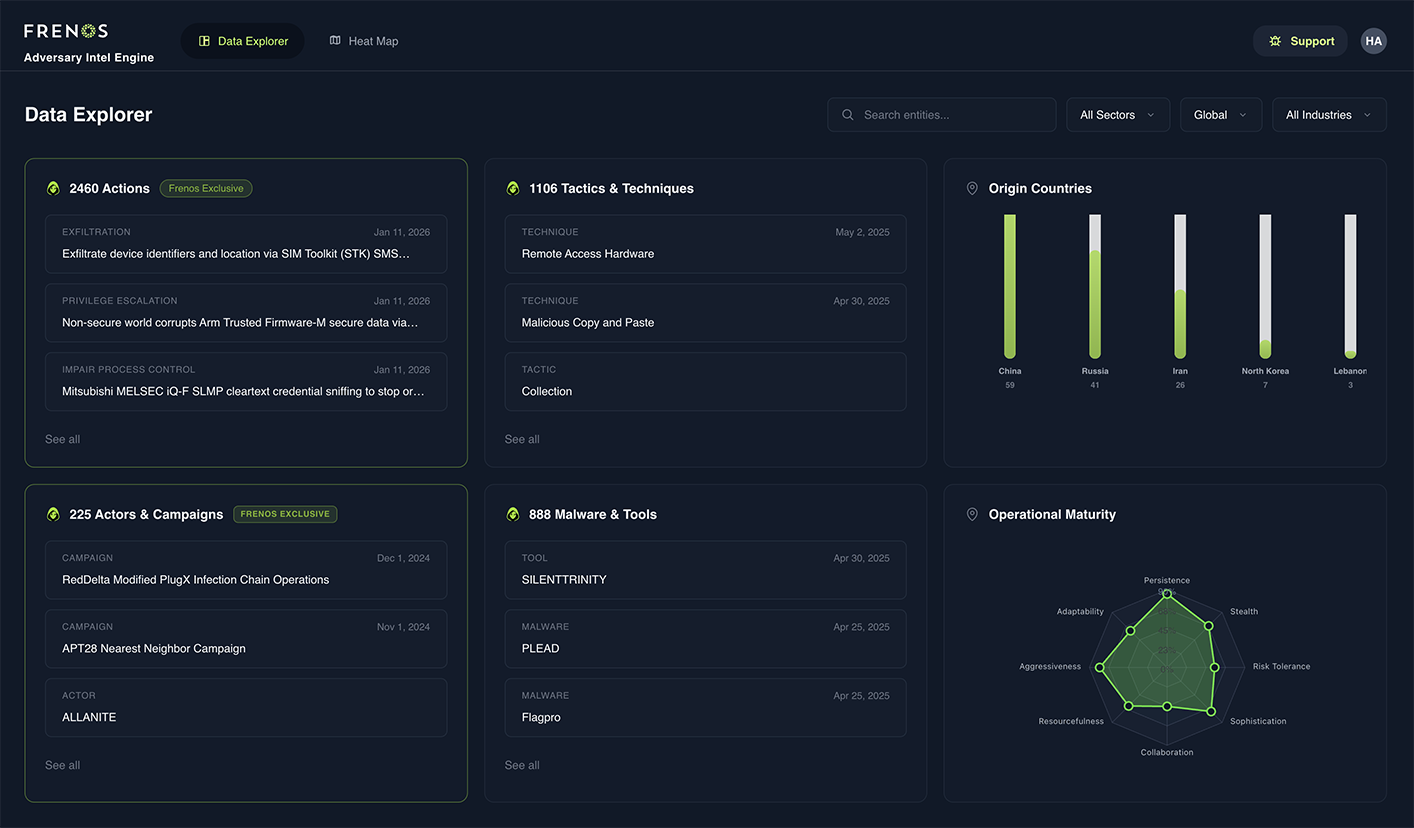
Data Explorer
Drill into actors, actions, and evidence to trace how attacks unfold step by step.
Examine the requirements needed for Exploitation and privileges gained after.

Heat Map
Identify concentration of adversary activity by tactic, impact, and operational maturity to prioritize defensive focus.
Determine adversary TTP overlaps and which actors operate the same.
Catalog Outputs and Governance
Intelligence you can trust, audit, and operationalize.
WHAT WE GENERATE
Actor Profiles
Evidence-backed summaries compiled across many documents to capture who the actor is, where they operate, and how they tend to behave.- Normalized attributes: aliases, regions, sectors, campaigns, and tooling
- Transparent provenance: profiles link back to supporting documents
- Built for automation: consistent fields suitable for downstream systems
Attack Library (Threat Actions)
Structured action definitions derived from technique analysis, designed to be reusable across detection, response, and risk workflows.- Prerequisites: (environment, software, and vulnerability conditions) captured at a high level
- Outcomes describing what changes when the action succeeds (by tactic category)
- Detection cues and supporting evidence stitched into each action
Quality, Compliance & Safety
Reference Expansion
Before analysis, documents are enriched by following embedded links and capturing clean, analysis-ready content with caching to reduce rework.- More coverage by including cited external material
- Better grounding so enrichment is based on fuller context
Post-Batch Review
- Semantic deduplication to keep the action catalog clean and consistent
- Quality scoring to flag weak or incomplete entries for improvement
- Approval gates with audit trails for changes
SAIRA RESEARCH
After the initial batch, SAIRA Research continuously improves threat actions through an iterative research loop. Each action is validated, enriched with external research, and re-validated until quality thresholds are met.
Initial Threat Action
Raw action from SAIRA Max enrichment
Search Engine Research
External sources queried for supporting evidence
Update
Action enriched with new findings
Validation
Schema checks and quality scoring
Testimonials
“I don’t need more intelligence. I need intelligence I can use. Frenos distills the data to the what and the how, which is exactly what makes it operationalizable.”
OT Cyber Architect
Southeast US“We want to give back to the community something we wish we had when we were practitioners. By releasing a community version of how our AI agent SAIRA operates, we’re showing our work.”
Harry Thomas
Co-Founder and CTO of Frenos"Intelligence only matters if it drives decisions. Frenos bridges ICS gaps left by MITRE ATT&CK, modeling real adversary actions and making that intelligence actionable for simulations."
Tony Turner
VP of Product, FrenosAdversary Intel Engine: Frequently Asked Questions
General
What's Inside the Catalog
- 2,400+ Threat Actions: Structured action definitions derived from technique analysis, each with prerequisites, outcomes, and detection cues.
- 174 Actor Profiles: Evidence-backed summaries covering who the actor is, where they operate, and how they behave.
- 1,106 Tactics & Techniques: Mapped across the MITRE ATT&CK framework, including ICS-specific tactics.
- 225+ Actors & Campaigns: Tracked with normalized aliases, regions, sectors, and tooling.
- 888 Malware & Tools: Cataloged and linked to the actors and actions that use them.
- Prerequisites: The environment, software, or vulnerability conditions required for the action to succeed.
- Outcomes: What changes when the action succeeds, organized by tactic category.
- Detection cues: Signals and evidence that defenders can use to identify the action.
How It Works
- Source Intake: Threat reports, advisories, knowledge bases, and curated collections are ingested.
- Extract & Version: Text is extracted (including from PDFs), with change detection and provenance tracking.
- Reference Expansion: Embedded links in documents are followed and captured to enrich the source material with cited context.
- Normalize: Strict schemas and consistent IDs are applied across documents, actors, and techniques.
- SAIRA Max: AI-driven classification of documents, analysis of actors and techniques, and generation of structured threat actions.
- Review & Enhance: Deduplication, quality review, and continuous improvement via the SAIRA Research agent.
- SAIRA Max handles the initial heavy lifting. It classifies documents, analyzes actors and techniques, and generates structured threat actions at scale.
- SAIRA Research runs after the initial batch, continuously improving threat actions through an iterative loop. Each action is validated, enriched with external research, updated with new findings, and re-validated until quality thresholds are met.
- Strict schemas and validation ensure consistency across all catalog entries.
- Reference expansion enriches documents with the full context of cited sources before any analysis begins.
- Semantic deduplication keeps the action catalog clean by identifying and merging near-duplicate entries.
- Quality scoring flags weak or incomplete entries for improvement.
- Approval gates with audit trails track every change through the review process.
- 2-pass quality review with human-in-the-loop combines automated checks with expert oversight.
Community Edition
Support
Have a question that's not answered here? Contact us at info@frenos.io.
