Continuous OT Security Posture Management (OT-SPM) Platform
From Annual Assessments to AI-Native Proactive Continuous OT Defense
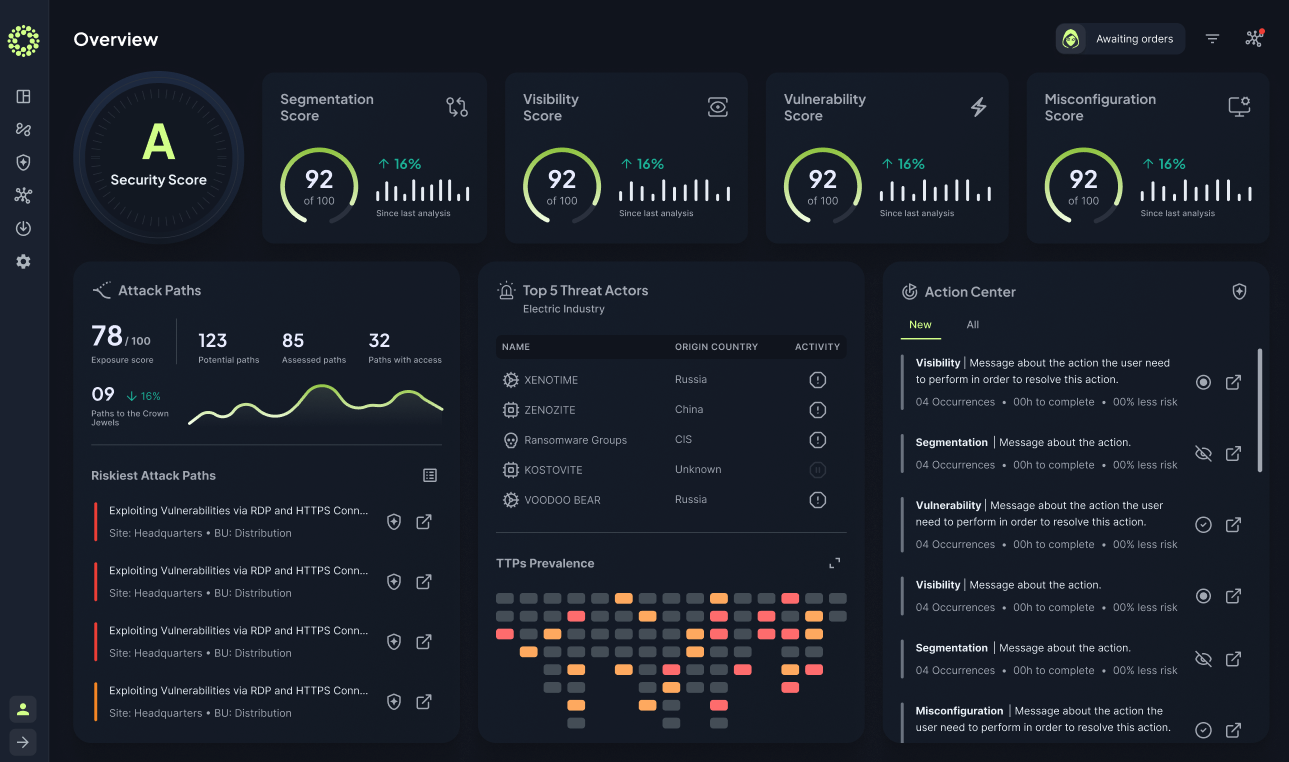
Your OT infrastructure never sleeps; neither should your security validation. The Frenos Continuous OT-SPM Platform transforms how enterprises manage OT security risk, providing real-time security posture trending across hundreds or thousands of OT environments.
By creating a digital twin of your operational networks, Frenos enables security teams to continuously assess, prioritize, and defend against evolving threats without ever touching production systems. This revolutionary approach replaces outdated point-in-time manual assessments with always-on AI adversary attack simulation within a digital twin that adapts as your environment changes.
Key Benefits
Automated and Continuous OT Assessments
Integrate Frenos' OT-SPM platform with your existing security tools and schedule weekly, monthly, or quarterly security posture assessments
Trend Your OT Security Improvements
Have the ability to show how your security mitigation activities are improving your OT security risk posture
Reduce Labor Hours + Save Time
Automate required annual security assessments in minutes versus months while saving time and money
Shift from Reactive to Proactive OT Defense
Start today by focusing on proactive mitigations that will deter the most likely adversary techniques and tactics by simulating threat intelligence feeds against your environments' digital twin

Continuous Security Posture Trending
Prove the value of your security program with visual trends showing risk reduction over time, enabling data-driven decisions and demonstrating measurable improvement to stakeholders
Analyze and Visualize Potential Attack Paths
Understand your most probable attack paths and visualize the most likely TTPs allowing an attacker into your critical environments
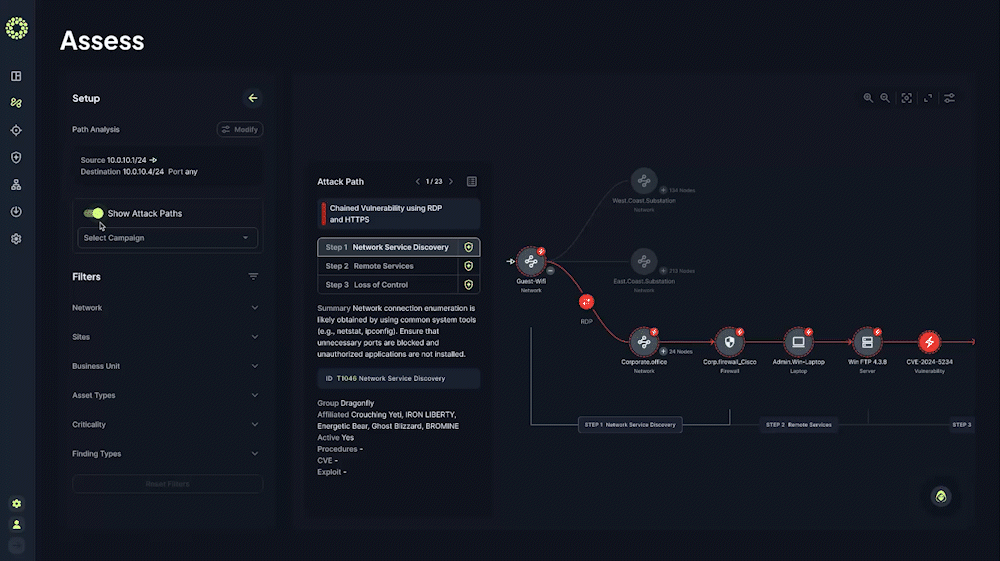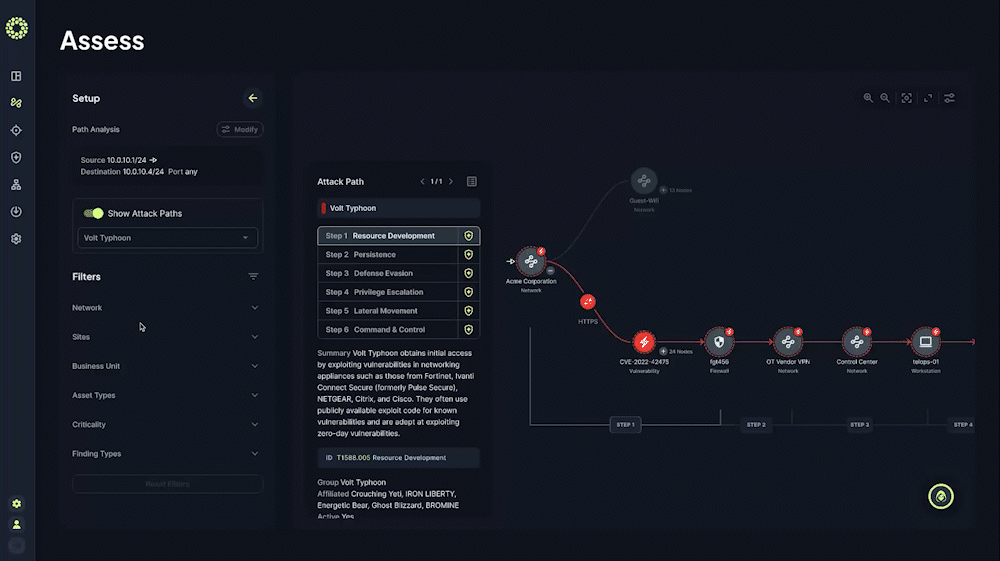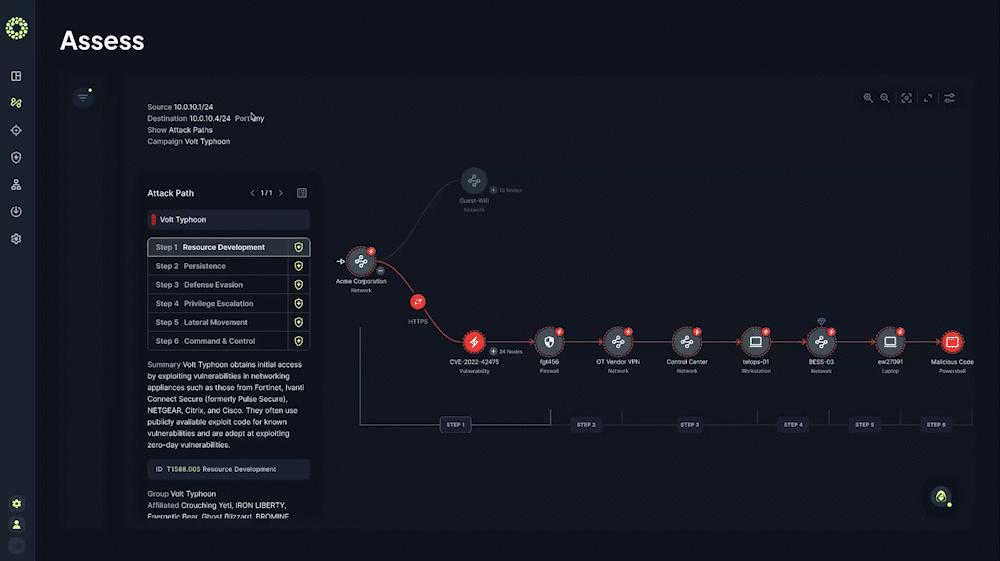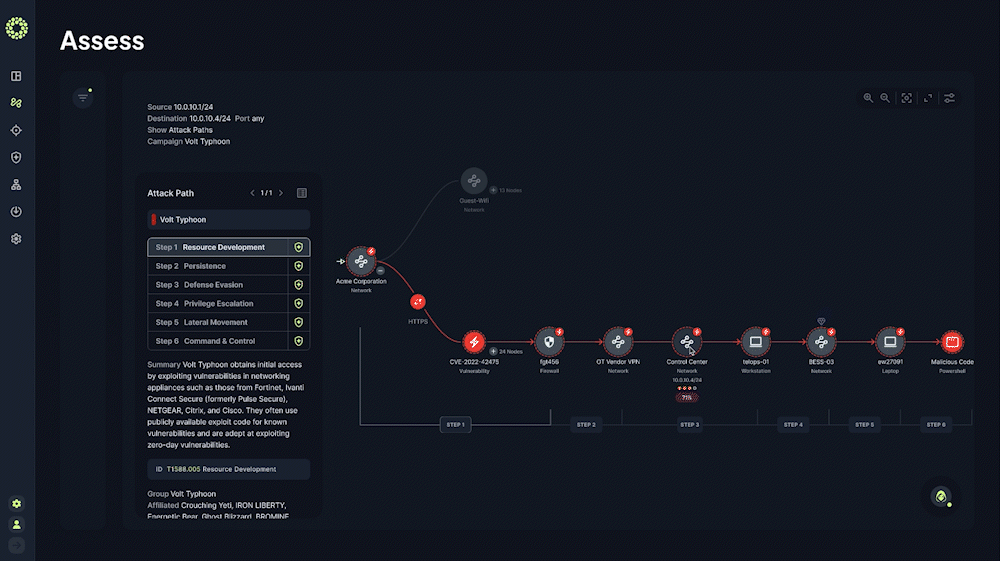
Prioritize Security Mitigations Based on Business Impact
See a list of prioritized proactive risk mitigations categorized by specific cybersecurity functions
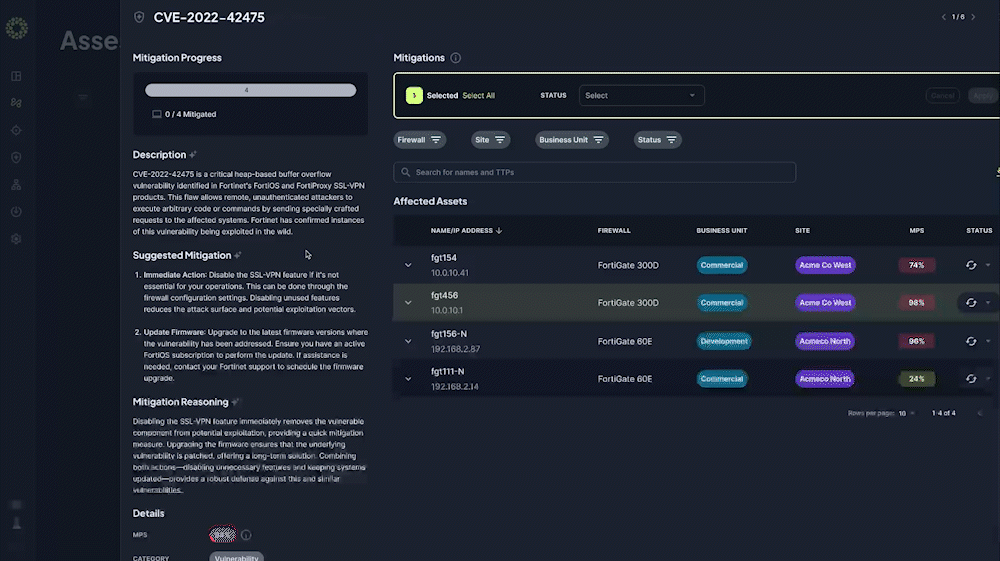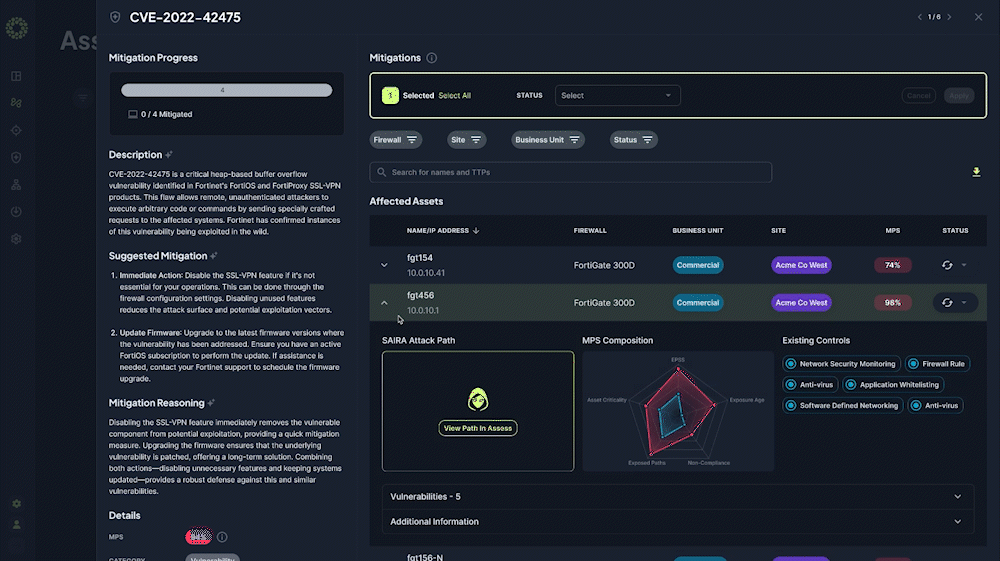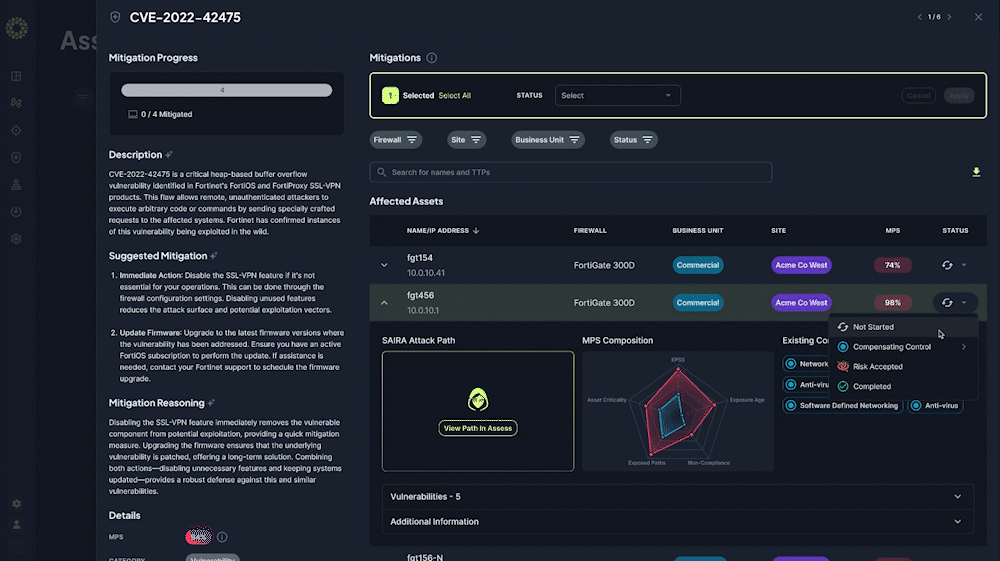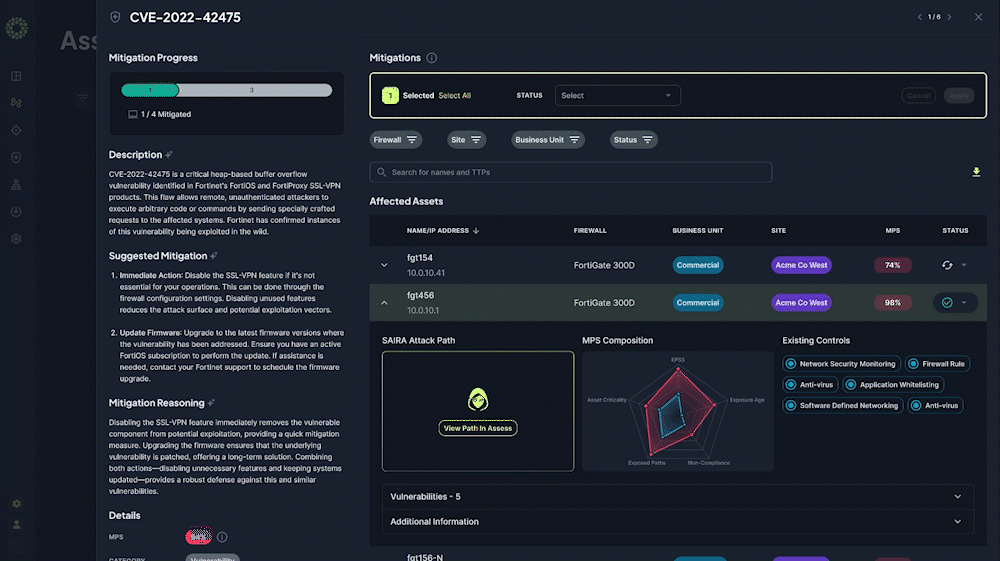
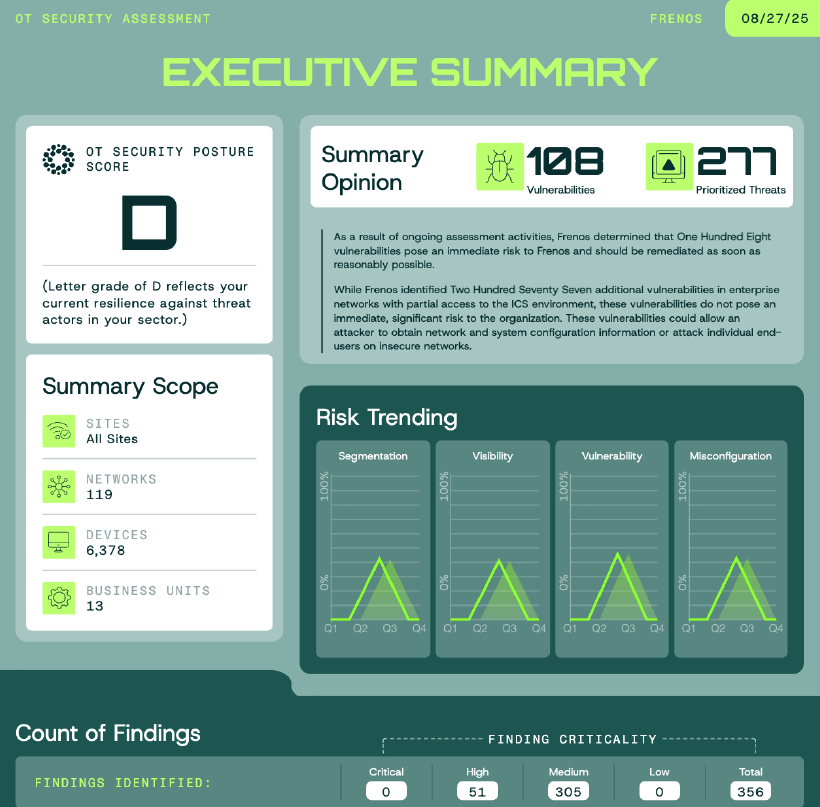
Automated Security Assessment Reports
Transform manual annual assessments into automated monthly or quarterly reports saving 200+ hours of work, reducing costs by 85%, and providing continuous compliance documentation at the click of a button
Resources


Get in Touch with Our Team
Strengthen your organization's ICS/OT cybersecurity defenses with our OT security security posture management platform




