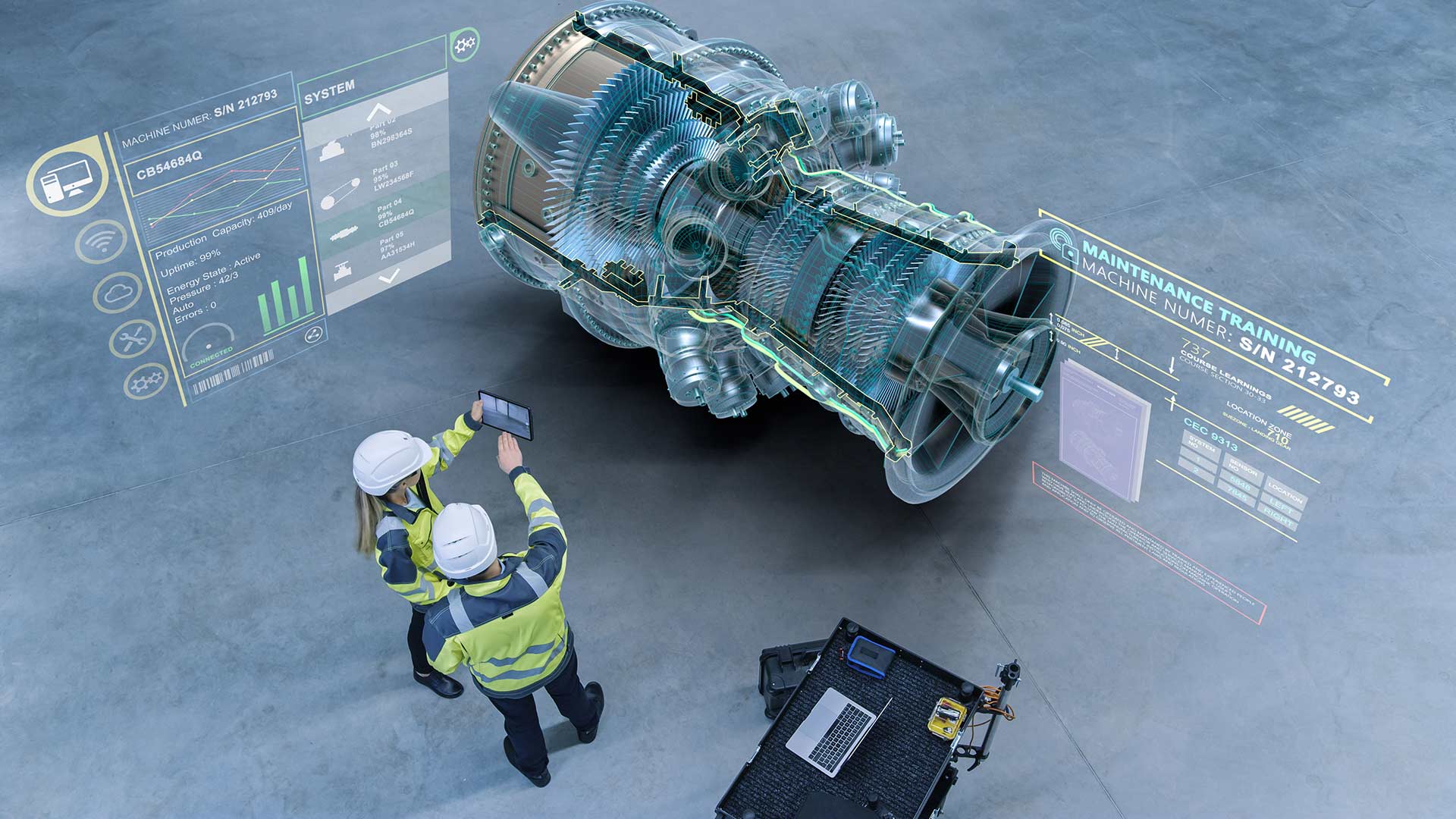
Rapidly scale evaluation capabilities across complex industrial environments without compromising operational integrity
A Theory of Evolution
We can all think of processes that started with paper and pencil, moved to personal computers and spreadsheets, and now happen almost without intervention on devices that fit in our pockets. For example, people used to have a paper-based address book, which was painstakingly updated whenever new contacts were added or existing contacts moved or changed. And there was that nifty thing called a “Rolodex”, with removable paper cards on a rotating dial used in offices. As computer automation became more available to individuals, people would enter their contact information electronically into a spreadsheet or a simple application on their computer. Now, your laptop, tablet, and phone monitor your calls, emails, and texts and automatically enter (or suggest) information to add to your contact list when it is encountered— an example of moving from a manual to an automated to a continuous process. This makes the data easier to maintain and more reliable and accurate.
Our theory is that OT security assessments need to evolve similarly. Because let’s face it, the security of your OT environment is wildly more complex than the names, addresses, and phone numbers of your friends, family, or business associates.
To stay ahead of rapidly evolving threats and maintain critical infrastructure's safety and reliability, you should implement the most advanced assessment technology possible.
Here’s why:
Manual assessments require extensive labor hours for data collection, analysis, and report generation, which can take weeks or months. Differences in experience, fatigue, and focus can lead to inconsistent results and missed vulnerabilities. They struggle to keep pace with the complexity and scale of modern OT environments, especially in large organizations with multiple locations and systems. Manual vulnerability assessments often provide delayed feedback, potentially leaving organizations vulnerable to attacks during the assessment window.
Automation can reduce the time and effort required for assessments, providing faster insights into vulnerabilities and risks. Automated assessments apply the same criteria and checks across all systems, minimizing human error and ensuring consistent results. Automated tools provide improved visibility into the security landscape, enabling more timely interventions and threat mitigation. Automated assessments are more scalable and cost-effective than manual assessments but leave room for improvement.
So . . . how do we do even better?
Continuous assessment, leveraging automation and real-time data, provides immediate visibility into the security landscape, enabling proactive threat mitigation and adaptation to a dynamic threat landscape. Which sounds much more like 2025, doesn’t it?
Moving Beyond Assessment Intervals
-
Proactive Threat Mitigation
Continuous monitoring and assessment enable organizations to identify and address vulnerabilities before they can be exploited. -
Adaptability to Evolving Threats
Continuous assessment allows organizations to quickly adapt to changes in the threat landscape and maintain a strong security posture. -
Compliance with Regulations
Continuous monitoring helps organizations meet compliance requirements by ensuring that security controls are consistently applied and effective. -
Optimization of Security Investments
Continuous assessment helps organizations optimize their security investments by providing data-driven insights into the effectiveness of their security controls and resources.
For example, the Frenos Zero Operational Impact Platform helps critical infrastructure operators understand which techniques, tactics, and procedures (TTPs) and associated vulnerabilities pose the greatest risk, performing as an OT vulnerability assessment tool. This empowers security teams to focus on the most critical activities, saving time, money, and resources. This platform continuously assesses the security posture of environments at scales unachievable by red teams, consultants, or third parties without putting a single packet on your network. All that is required is data from your existing cybersecurity solution providers, ensuring zero impact to your operations.
The Evolution Revolution
Many organizations have gone through this evolution in OT cybersecurity assessments. A key commonality is that the increasing sophistication of cyberattacks against critical infrastructure demands a fundamental shift in how organizations approach cybersecurity.
As a reference point, there is a comparable cybersecurity category of products in IT called Penetration Testing as a Service (PTaaS). Enterprise IT companies are leveraging PTaaS technologies to evolve their assessment strategies. This case study exemplifies how South Staffordshire College implemented a continuous assessment strategy with Pentera. This automated penetration testing platform provides the ability to run continuous, automated penetration tests, enabling on-demand network “pen-tests” to detect the most critical security needs in the environment. In the study's conclusion, we find it notable how the South Staffordshire College IT department has established itself as the technological forefront in security technologies and dealing with security risk. While active penetration testing technology itself isn't used in OT because it causes outages, it is driving the need for Frenos' zero operational impact approach to OT assessments. We find the evolution of the approach interesting in and of itself.
Traditional reactive security measures – including manual and automated processes – are no longer sufficient to protect essential services and operations from determined adversaries.
The Frenos proactive defense framework demonstrates how organizations can implement a proactive defense strategy that anticipates and prevents attacks before they can impact critical systems. Integrating comprehensive threat intelligence with practical validation through simulation creates a powerful feedback loop that drives continuous security improvement. Organizations can anticipate likely attack vectors and implement targeted defensive measures by understanding and analyzing current threats through industry partnerships and intelligence sharing. This intelligence-driven approach ensures that security resources are focused where they will have the greatest impact in preventing successful attacks.
Security Without Blind Spots
In a previous Blog, we asserted that modern critical infrastructure protection demands a fundamental shift from 'detect-and-respond' to 'predict-and-prevent', and we painted a picture of what that looks like:
- Continuous attack surface analysis that accounts for constant internal security controls and external threat changes
- Integration of industrial threat intelligence to identify emerging tactics, techniques, and procedures before they're weaponized
- Automated validation of security controls against current threat actor methodologies
- Real-time analysis of potential attack paths considering both IT and OT network topologies
The Ultimate End Goal: Continuous Security Assessment
That blog also has a “checklist” that suggests steps you can take to implement a successful Continuous Assessment environment. We think every organization should empower its OT Security teams to precisely identify and prioritize the most impactful risk-reducing cybersecurity mitigations, ultimately strengthening OT infrastructure resilience while optimizing resource allocation.
We have also discussed how a Continuous Assessment approach fits into an organization's overall, holistic approach to Risk Management. When an organization evolves to a continuous assessment process, it can feed directly into its broader risk management program, driving updates to defensive controls and security policies as needed.
The Continuous Assessment Advantage
Is your OT Cybersecurity program keeping up with today’s potential threats? Or are you stuck with a “Rolodex”-class assessment process?
Evolving your assessment processes increases your chances of avoiding attacks. Whether you are still using “pen and paper”, have adopted some level of automated processes, or are considering moving to a more integrated, continuous assessment model, we at Frenos would like to be a part of your OT Cybersecurity assessment journey. Contact us at Frenos to find out more.